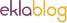-
Tightvnc Failed To Connect To Server Windows Vista
The RPC Server Is Unavailable. Attention. Before you read this tutorial, I highly recommend you check out my resources page for access to the tools and services I use to not only maintain my system but also fix all my computer errors, by clicking here! Before you can fully understand the function(s) of the RPC server, you will first need to know what an RPC is, such as its attributes and importance. RPC is an abbreviation of the words Remote Procedure Call. It’s basically a technology that utilises a communication technique called inter- processing, which is used for enabling a server and client PC to communication with one another over a network. The basis of this protocol is the client/server model, which means data is packaged and distributed through this communication technology to other processes that do not exist on the same process (computer). The way in which it works is pretty simple: a procedure call is made, by a client computer; this call appears as though it was made locally, but is in fact made by a remote computer.
The RPC Server Is Unavailable. Attention. Before you read this tutorial, I highly recommend you check out my resources page for access to the tools and services I use to not only maintain my system but also fix all my computer errors, by clicking here! Before you can fully understand the function(s) of the RPC server, you will first need to know what an RPC is, such as its attributes and importance. RPC is an abbreviation of the words Remote Procedure Call. It’s basically a technology that utilises a communication technique called inter- processing, which is used for enabling a server and client PC to communication with one another over a network. The basis of this protocol is the client/server model, which means data is packaged and distributed through this communication technology to other processes that do not exist on the same process (computer). The way in which it works is pretty simple: a procedure call is made, by a client computer; this call appears as though it was made locally, but is in fact made by a remote computer.
During this process, the data for the call is then encrypted and sent to the server. It is then decrypted and run by the server. A return value is then passed back to the client PC, which is determined by the initial data type that was sent to the server. This concept of compartmentalising network operations into procedure calls is a concept that was invented way back in the 1. Xerox being the very first machine to utilise this technology under the UNIX operating system. RPC technology is most important for those individuals that would like to share access to a printer over a network or manage computers within a network remotely. IT Support professionals are also known to use RPC services for managing computers remotely.
To do this, they use the Remote Desktop feature on Windows. Any process which involves the distribution and sharing of data usually uses this technology. With that said one of the main drawbacks of RPC technology is that remote calls are known to regularly exhibit intermittent performance, and for a plethora of reasons; leaving you none the wiser when it does occur. Common Causes of This Error. The RPC server requires a few services to be running in the background in order for it to function. If you’ve received “The RPC Server Is Unavailable” message then it’s likely due to maybe one or two services that the RPC server depends on for it its functionality, not working/running or it could be the result of file corruption. Alternatively, the unavailable message you’re receiving could be due to registry corruption or all three, in which case you would be required to do quite a lot of troubleshooting to solve the issue.

Anyway, with that said, the most common causes are as follows. RPC related services have stopped running. File and printer sharing has been disabled. A network connectivity issue.
Registry data required for the RPC service has become corrupted. Given the circumstances, the best you could ever hope for is the issue being due to your inability to properly configure both processes to communication with one another. There are a number of items that you have to ensure are properly configured when attempting to use the RPC service, which means there’s equally as much troubleshooting to do when attempting to solve an issue with this service.
In the past, there were a plethora of malware and viruses floating around the internet that were designed to exploit your system through the security holes that resulted from using the RPC service. However, today, RPC is significantly safer, owing to all the proceeding security updates. Automated Solution. Issues with the RPC service can be the result of a number of things.
The cause of the issue varies depending on the specifications and configuration of your computer(s). This makes it increasingly difficult for you to pinpoint the exact cause of the problem. In addition, attempting to fix the problem manually can be a momentous task for most people, and in some cases, dangerous, if you’re a novice computer user. Fortunately, there are a number of automated tools that you can use, such as Speedy. PC Pro. Speedy. PC Pro is a multifaceted registry cleaner program, which is capable of defragging your systems hard drive, speeding up your internet connection and freeing up hard drive space by removing unwanted clutter, cleaning the Windows registry and tackling issues such as the one you’re currently bogged down with, amongst others.
You can find out more about this tool here: CLICK HERE TO CHECK OUT SPEEDYPC PROManually Fixing the RPC Server. It’s recommended that you at least try the automated approach before attempting to fix it manually.

With that said, to follow is a step- by- step guide that you can use to hopefully fix this problem. In this guide I will take you through a number of steps that will identify common causes for this error and provide recommended solutions for rectifying it. The steps are arranged in order of priority, which means you should start from the top and work your way down. Check Your Firewall. If you have a third party firewall program on your computer, then there is a good chance that it could be blocking RPC requests. Thus, you will need to go through your firewall program and ensure that it’s been configured to allow outgoing and ingoing connections and that any applications that you intend to use with this service is set to trusted.
Have you received the following message “the RPC Server is Unavailable”? Well in this tutorial, I’ll take you through a number of techniques that you can use to. ColdFusion, Flex, Ajax and other items of interestFix for Filezilla Failing to Retrieve Directory Listing. Everyone loves a good laugh, and in the age of electronics, high-tech hijinks are just waiting to be pulled off. So snuggle up to your screen and get ready to unleash.

If you’re unable to reconfigure your firewall program, then you could consider turning the firewall program off, temporarily, that way you can find out whether it truly is the firewall causing the problem, when you reattempt an outgoing procedure call. Alternatively, if you’re using Windows Firewall, then you should make sure an Exception for Remote Desktop has been made and is enabled. To do this, simply do the following.

Troubleshooting Windows Instances. The following procedures and tips can help you troubleshoot problems with your Amazon EC2. 1 Legal Information. This document and all associated illustrations are licensed under the Creative Commons Attribution 2.5 License. Any works which contain material.
Remote Desktop Protocol: What it is and how to secure it. Recent flaws in Remote Desktop Protocol (RDP) have shined a spotlight on the remote access protocol.

First, ensure you’ve logged into your computer with administrative rights. Then click on Start - > Control Panel. Once Control Panel loads up, double click on Security Center.
Once Windows Security Center loads up, click on Windows Firewall. The applet for Windows Firewall should pop up, from here, click on the Exceptions Tab, then check the box next to Remote Desktop and click on OK. Note: The Remote Desktop Exception is created by default; all you need to do is ensure it’s enabled and if not, enable it.
Run Windows Update. I talk about this quite a lot when it comes to fixing a whole plethora or computer issues. Before attempting any other solution(s), it’s very important that your computer has all the latest updates installed on it. To check for the latest updates, simple go to Microsoft’s Windows Update site here: http: //windowsupdate. Check Internet Protocols.
The first thing you’ll want to do is ensure that the special drivers are installed properly, as they are used for internetworking. The likelihood of you having problems with the drivers is fairly low, but it doesn’t hurt for you to check. This can be done by doing the following. First, ensure you’ve logged into your computers with a user profile that has administrative rights.
Then click on Start, right click on My Network Place and select Properties. This will bring up Network Connections, from here, right click on Local Area Connection and select Properties. The Local Area Connection Properties applet will load up. From here you’ll want to ensure that under this connection uses the following items: you have Internet Protocol (TCP/IP) and File and Printer Sharing for Microsoft Networks. Note: If either one of these items is missing, then you will need to reinstall them. For information on how to reinstall new items, check out my post on how to fix the Winsock errors. Verify Your Drivers.
After you have verified that you have all the appropriate items installed in your internet connection, the next thing you’ll want to do is ensure that they are all working correctly. This can be done by doing the following. First, ensure you’ve logged into your computer with administrative rights. Then click on Start - > Run, type cmd and click on OK. When Command Prompt loads up, type Verifier /Driver and hit Enter. Once the process has finished, restart your computer.
You should then check to see whether the issue has been rectified. If not, proceed to the next step.
The RPC requires a few services to be running in the background before it can function. The steps below will outline the exact services that should be running on your operating system before you can expect the RPC service to work. First, ensure you’ve logged into your computer with administrative rights.
Then click on Start - > Run, type services. OK. This will bring up the Services applet. From here you’ll want to verify that the appropriate services are running on your computer. If you find that a required item is not running on your computer, then you should double click on it to bring up its Properties applet. Then on the General Tab, select Automatic from the drop menu next to Startup type: and then click on the Start button followed by Apply and OK. The following are the services that should be running on your computer based on the version of Windows your using: OSService. Startup type. Windows XPRemote Procedure Call (RPC)Automatic.
Windows Vista. Remote Procedure Call (RPC)Automatic. DCOM Server Process Launcher.
Automatic. Windows 7. Remote Procedure Call (RPC)Automatic. DCOM Server Process Launcher. Automatic. RPC Endpoint Mapper. Automatic After you have verified that all the required services are running, you should then attempt to use the RPC services.
If you’re no longer getting the error message, then the issue has been solved. However, if it persists, the continue reading. Verify Your Registry. There are a few entries that should exist within the Windows registry for the RPC to work.
If any of these entries were to become corrupted, then the RPC service would cease to function.
How to secure RDP network endpoints. Remote Desktop Protocol: What it is and how to secure it. Recent flaws in Remote Desktop Protocol (RDP) have shined a spotlight on the remote access protocol. In fact, noted.. By submitting your personal information, you agree that Tech. Target and its partners may contact you regarding relevant content, products and special offers.
As you can imagine, if enterprises don’t properly secure RDP, network and endpoint security can be compromised. In this tip, I’ll briefly examine what RDP is, why it’s needed, and how it is most often used on enterprise endpoints. I will then examine how enterprises can ensure RDP is used securely or, when appropriate, how to ensure it’s not in use. What is RDP? Remote Desktop Protocol is a proprietary protocol created by Microsoft. It allows a system user to connect to a remote system with a graphical user interface. The client- side agent is built into the Microsoft operating system by default, but can be installed on non- Microsoft operating systems, such as those from Apple, various flavors of Linux, and even mobile OSes like Android. This can either be for management, remote access or publishing an application for central use.
It’s this specific function that can become an issue if not configured properly, allowing unauthorized access to key enterprise systems. How to secure RDPNow that we understand what RDP is and how organizations use it, here are a few ways to secure RDP implementations: Verify 1. By default, the RDP connection will try to use 1. As a precaution to verify systems won’t fall back to a lower level of encryption, administrators can configure Group Policy Objects (GPOs) to have the encryption level set to their individual standard.
It’s recommended that it’s enabled to “High Level.”If access to a system is needed via the external network, instead of leaving the port open for anyone to abuse, configuring a VPN to tunnel back into the network and then using RDP is recommended. Even better than this would be to create a remote desktop gateway that would allow remote connections using HTTPS and the RDP to create a more secure and encrypted connection to the endpoint. Both of these methods are recommended over leaving RDP port 3. With newer versions of Windows operating systems (Vista, Windows 7 and Server 2. NLA) as an additional layer of authentication before establishing a connection to the RDP host server. This takes the authentication away from the system and uses fewer resources. It is possible to change the listening port of the RDP service, which would protect the network from any malware or attackers scanning systems for RDP on port 3.
However, this “security by obscurity” approach can lead to errors and oversight. It’s possible to change the port, but you need a good reason for doing so. Using firewalls either on the perimeter or on the OS to filter incoming requests to only approved sources and permitted destinations via RDP connections can limit who can actually connect to these servers. If there’s a particular group of people that are only supposed to connect to a particular group of servers, wrapping firewall rules around these requests will help contain access. Verify who’s capable of creating an RDP connection to a server. Consider restricting RDP access to specific groups (via Group Policy or manually on target machines) instead of leaving it open to everyone. Restricting access, too, is always preferable.
Also, removing the local admin account from RDP access is recommended. All users’ accounts should be clearly defined on the system ahead of time. While NLA performs some form of authentication, using SSL certificates to authenticate a client request to a host system is the best method of authentication available for RDP. Installing the certificate on the system and the RDP client will allow certificate authentication before an RDP session can be established. Verify all patches to systems running RDP are up to date, especially after the recent events resulting in Microsoft security bulletin MS1. Lastly, use GPOs to force a password policy to allow a certain password length in the domain and set a lockout policy to stop hackers from tying to brute force their way into a server. Defending against rogue RDP use.
The above- mentioned methods are ways in which an organization can secure the use of RDP in an organization. Now, let’s take a look at a few ways a company can verify RDP isn’t in use to protect itself against rogue or unauthorized installations of RDP. Running vulnerability or port scans across the network, both internally and externally, can help decipher if there are any systems listening for RDP connections. Running these scans internally can help show which systems are running RDP. It’s then up to a company’s team to verify if they’re supposed to be running this software. From an external point of view, if scans show up with RDP listening from the outside, it’s a queue to take action as soon as possible. Many vulnerability scanners will find RDP running on non- standard ports, so that will help if someone is trying to hide the installation.
Using logging or a security incident and event management (SIEM) system to verify what devices are listening and accepting RDP sessions can give your organization insight into what type of RDP connections are occurring on the network. Are others accepting connections that shouldn’t be? Lastly, the best method to ensure systems aren’t using RDP inappropriately is by defining a Group Policy that allows only approved systems to run the RDP.
In conclusion, RDP is a great tool used by administrators and users alike to establish multiple connections to a system from a centralized location. It’s also used by admins for remote systems management, but just like anything else, if the connections and software aren’t secure, companies are putting themselves at risk. Knowing how RDP works, why it’s being used, and what can be done to secure it will allow administrators to get a better hold of securing their systems. About the author: Matthew Pascucci is an information security engineer for a large retail company where he's involved with vulnerability and threat management, security awareness and daily security operations.
He’s written for various information security publications, has spoken for many industry companies, and is heavily involved with his local Infra. Gard chapter. You can follow him on Twitter at @matthewpascucci or check out his blog at www.
-
Commentaires